Audit Logs
Audit Logs provide a record of system activities and account actions within DebtRecoup.
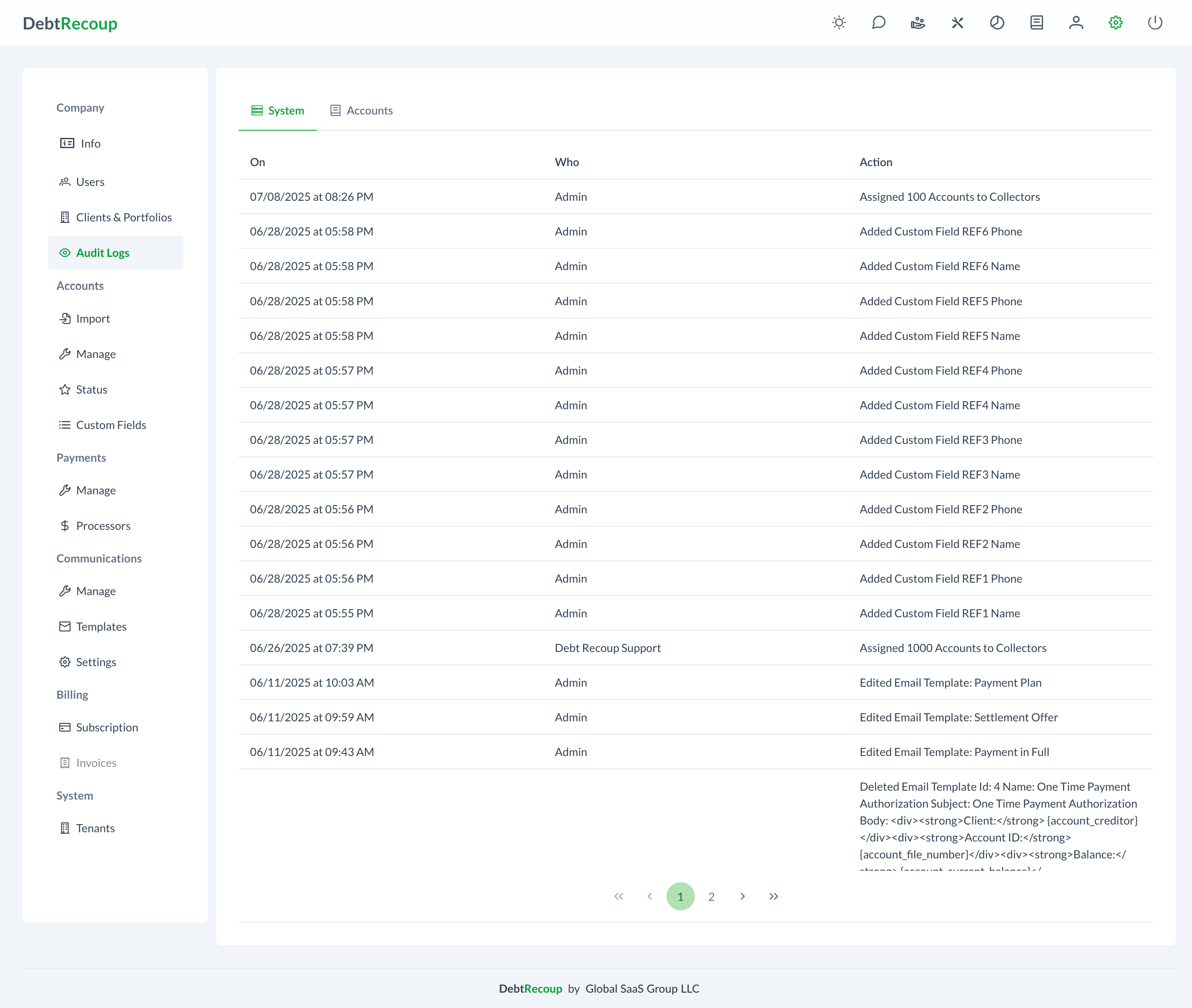
Accessing Audit Logs
- Click the Administrator button (gear icon) in the top navigation bar
- Select Company from the left sidebar
- Click on Audit Logs
Log Display
The audit logs interface shows two tabs:
System Tab
Shows system-level activities such as:
- User logins
- Configuration changes
- System events
Accounts Tab
Shows account-level activities such as:
- Status changes
- Payment recording
- Note additions
- Contact updates
Log Entry Fields
Each log entry displays:
| Column | Description |
|---|---|
| When | Timestamp of the action |
| Who | User who performed the action (or "System") |
| Action | Description of what occurred |
| File # | Account file number (Accounts tab only) |
Filtering Logs
Account Logs Filtering
When viewing the Accounts tab, you can filter by:
- Client - Show logs for a specific client's accounts
- Portfolio - Filter by portfolio
- Assigned To - Filter by collector assignment
Pagination
Logs display 50 entries per page. Use the pagination controls to navigate through results.
Using Audit Logs
Track Account Changes
- Click the Accounts tab
- Optionally filter by client, portfolio, or collector
- Review the activity history for matching accounts
Review System Activity
- Click the System tab
- Review login attempts and system events
Best Practices
- Review audit logs periodically for unusual activity
- Use client/portfolio filters when investigating specific accounts
- Check logs when troubleshooting account issues
Related Documentation
- User Management - Managing user accounts
- Company Settings - System configuration